Importance of Administration Port on WebLogic
This feature is very important for WebLogic domain management but WebLogic admins usually don’t take advantage of “WebLogic Administration Port” property.
I am highly recommending enabling “Administration Port” for WebLogic domains which have high transaction traffic.
Why WebLogic Administration Port?
By enabling Administration Port, you can separate administration traffic from application traffic in your domain. That’s fair enough to switch your WebLogic management to administration port.
Oracle Documentation: In production environments, separating the two forms of traffic ensures that critical administration operations (starting and stopping servers, changing a server’s configuration, and deploying applications) do not compete with high-volume application traffic on the same network connection.
How to do it?
- Firstly, shutdown all managed servers. This means for the production systems, you have to make a planned system work. If you don’t want to make and downtime do the restart job one by one.
- Click “Domain name” on the Domain Structure menu. On “$Domain_Name > Configuration > General” tab, then make “Enabled Administration Port” checked as below (No: 1). Change default port value to another, I’ve set it to 9902 (No:2)
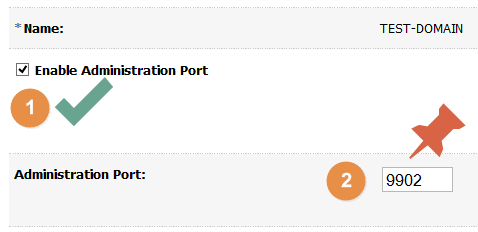
WebLogic Property: Enable Administration Port Click SAVE button.
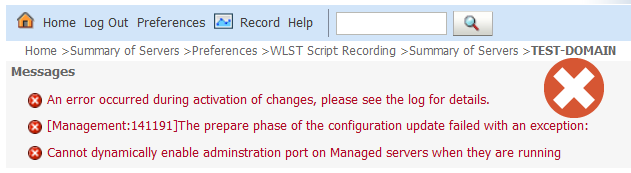
- Click on “Activate Changes” button.When WebLogic Managed servers are at RUNNING states, you’ll get below Warning. Just shut down ALL managed servers and try to activate again.
An error occurred during activation of changes, please see the log for details.[Management:141191]The prepare phase of the configuration update failed with an exception:Cannot dynamically enable adminstration port on Managed servers when they are running
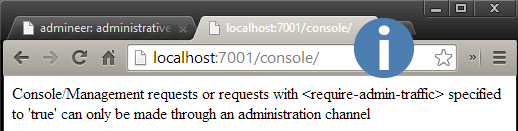
After the activation, Administration Port feature activated and you CANNOT use old port for accessing WebLogic console. You’ll see below screen after the activation.
WARNING on previous WebLogic console PORT: Console/Management requests or requests with <require-admin-traffic> specified to ‘true’ can only be made through an administration channel
WebLogic: Previous Admin Console Port / URL
WebLogic Administration Port Log:
####<Aug 13, 2015 6:50:08 PM EEST> <Notice> <Server> <maya01> <AdminServer> <[ACTIVE] ExecuteThread: ‘2’ for queue: ‘weblogic.kernel.Default (self-tuning)’> <weblogic> <> <> <1439481008557> <BEA-002613> <Channel “DefaultAdministration[1]” is now listening on 172.17.42.1:9902 for protocols admin, ldaps, https.>
Anymore you must USE the new administration port for accessing WebLogic console. My new address is https://localhost:9902/console.
REMEMBER:
The administration port accepts only secure, SSL traffic, and all connections via the port require authentication by a server administrator. Because of these features, enabling the administration port imposes the following restrictions on your domain:
- The Administration Server and all Managed Servers in your domain must be configured with support for the SSL protocol.
- All servers in the domain, including the Administration Server, enable or disable the administration port at the same time.
Errors: When you try to reach the domain by new https address, it’s possible that you CAN see below warnings on your browsers.
Chrome:
SSL server probably obsolete.
ERR_SSL_FALLBACK_BEYOND_MINIMUM_VERSION
Server has a weak ephemeral Diffie-Hellman public key
ERR_SSL_WEAK_SERVER_EPHEMERAL_DH_KEY
Firefox:
Secure Connection Failed
An error occurred during a connection to 10.100.3.227:7002. The server certificate included a public key that was too weak. (Error code: ssl_error_weak_server_cert_key)
The page you are trying to view cannot be shown because the authenticity of the received data could not be verified.
Please contact the website owners to inform them of this problem.
Internet Explorer:
There is a problem with this website’s security certificate.
The security certificate presented by this website is not secure.
Security certificate problems may indicate an attempt to fool you or intercept any data you send to the server.
We recommend that you close this webpage and do not continue to this website.
SOLUTIONS:
* If you get above errors while accessing WebLogic https console, you must regenerate your default keystore and trust with 2048 key size.
* If you still cannot access to WebLogic administration port SSL console, just make sure that your WebLogic Admin Server’s ListenAddress is set properly. Otherwise, kill AdminServer process, then set your ListenAddress manually by editing config.xml.
If you still cannot login to Admin console, just rollback the Administration port feature by editing config.xml as below. I am listing some administration port errors below for people who facing these problems.
<administration-port-enabled>false</administration-port-enabled>
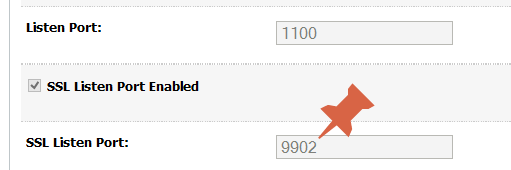
The following failures occurred: — [Security:090896] The SSL ListenPort attribute 9902 cannot be the same as the Administration Port for the server. Errors must be corrected before proceeding.
* If you want to access WebLogic 11g (10.3.6) SSL console with default JKS and TURST, you can use Opera Browser for accessing. Opera still accepts default WebLogic JKS certificate configuration by accepting untrusted option.
WebLogic Administration Port WLST Connection:
You cannot access to WLST console with previous connection address, you must use new administration port address. Otherwise, you’ll get below error:
WLSTException: Error occured while performing connect : User ‘principals=[weblogic, Administrators]’ has administration role. All tasks by adminstrators must go through an Administration Port.
This Exception occurred at Wed Sep 11 10:08:37 VET 2015. javax.naming.CommunicationException [Root exception is java.net.ConnectException: t3s://localhost:7701: Destination unreachable; nested exception is: javax.net.ssl.SSLKeyException: [Security:090542]Certificate chain received from localhost – 0:0:0:0:0:0:0:1 was not trusted causing SSL handshake failure. Check the certificate chain to determine if it should be trusted or not. If it should be trusted, then update the client trusted CA configuration to trust the CA certificate that signed the peer certificate chain. If you are connecting to a WLS server that is using demo certificates (the default WLS server behavior), and you want this client to trust demo certificates, then specify -Dweblogic.security.TrustKeyStore=DemoTrust on the command line for this client.; No available router to destination] javax.naming.CommunicationException [Root exception is java.net.ConnectException: t3s://localhost:7701: Destination unreachable; nested exception is: javax.net.ssl.SSLKeyException: [Security:090542]Certificate chain received from localhost – 0:0:0:0:0:0:0:1 was not trusted causing SSL handshake failure. Check the certificate chain to determine if it should be trusted or not. If it should be trusted, then update the client trusted CA configuration to trust the CA certificate that signed the peer certificate chain. If you are connecting to a WLS server that is using demo certificates (the default WLS server behavior), and you want this client to trust demo certificates, then specify -Dweblogic.security.TrustKeyStore=DemoTrust on the command line for this client.; No available router to destination]
SOLUTION:
C:\Middleware1036\wlserver_10.3\common\bin>C:\Java\jrockit-jdk1.6.0_45-R28.2.7-4.1.0\bin\java –cp c:\Middleware1036\wlserver_10.3\server\lib\weblogic.jar -Dweblogic.security.SSL.ignoreHostnameVerification=true -Dweblogic.security.TrustKeyStore=DemoTrust -DskipWLSModuleScanning weblogic.WLST connect_and_list.py
connect_and_list.py
connect(“weblogic”,”welcome1″,”t3s://localhost:7701″)
ls()
Please comment and follow for new posts and problem solutions.
Have a good administration day 🙂



How do I disable all non-SSL ports on a 2-node weblogic cluster?
I am able disable on node 2 using the Admin Console. But when I do same for node 1, I get the non-SSL ports enabled again after activating and restarting the Admin Server and managed servers
Thanks for your assistance
Hi,
Before doing for node-1 have you activated the Administration port?
If some one wishes expert view about blogging after that i recommend him/her to go to
see this web site, Keep up the nice work.
This text is worth everyone’s attention. Where can I fijd out more?
The tradition of Feria began in 1847, in Sevilla.
I am using weblogic 10.6 , I can not activate changes when I press activate changes it gives: weblogic.management.provider.EditSaveChangesFailedException: Can not save changes while prepare changes are still in progress
Hi,
When we start an applicaton using “start serving only administration reequests”, then how to access the application- is it through the –
-admin host ip and administration port or
– the managed host ip and administration port
Hi,
When you enable “Administration Port” on managed server; each managedserver has its own “Local Administration Port Override”. You can access the application by using this alogirthm for its URI: ” http:// + managedServerIp + LocalAdministrationPortOverride + ApplicationURI”
You shared very key information on weblogic administration.I saved your post for reference in troubleshooting.Thank You.
Thank you madhav, keep contacting…
Hi Morten,
thank you for your feedback 🙂
Administration port is totally different from https port. “Server > SSL port” is used for application’s HTTPS traffic. But Administration port is used by WebLogic admin and managed servers via t3s protocol. It’s an internal protocol for managing application JVM container. By using administration port you are able to distinguish application traffic and WebLogic t3s traffic.
Hi Fevzi,
We don’t have much traffic on our domain. Do you recommend anyway?
Hi Van,
In this case, there is no need to activate administration port. But, if you would like to move your internal traffic to HTTPS, it would increase the security.
Regards..
Hi…very good blog
But what are the difference between the administration port and the admin server SSL port?
I have several domains using normal 7001 and ssl port 7002 and we wanted to secure access to wls console and two solutions came on the table….administration port 9002 or ssl port 7002
Hi Team,
I am using weblogic 10.3.6 and have one admin and 4 managed servers configured. On one of the managed server listening on SSL port 7299, one way SSL has been enabled with a certificate with key size 2048.
When I am trying to access applications deployed on ssl enabled managed server using Internet explorer 9, I am able to open the home page of application on SSL port but as soon as I press any button on GUI of the application it logs me out.
If I access same application on SSL port using Firefox 38.3.0, It shows the following error on browser
Server has a weak ephemeral Diffie-Hellman public key” or ERR_SSL_WEAK_EPHEMERAL_DH_KEY
If you see this error, it means that a secure connection can’t be established because of outdated security code on the website. Chrome protects your privacy by preventing you from connecting to these sites. You won’t be able to visit this page using Chrome.
If you’re a website administrator, we recommend you update your server to support ECDHE and disable DHE. If ECDHE is unavailable, you can instead disable all DHE cipher suites and rely on plain RSA.
Later I got some options that weakens the mozilla firefox security as below.
security.ssl3.dhe_rsa_aes_128_sha
security.ssl3.dhe_rsa_aes_256_sha
But after setting these variables false in firefox, my applications navigations are fine and works well.
I would add that when the https logs were captured using fiddler, I got to know the below
Client side ciphers available
Ciphers:
[C02B] TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
[C02F] TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
[C00A] TLS1_CK_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
[C009] TLS1_CK_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
[C013] TLS1_CK_ECDHE_RSA_WITH_AES_128_CBC_SHA
[C014] TLS1_CK_ECDHE_RSA_WITH_AES_256_CBC_SHA
[C007] TLS_ECDHE_ECDSA_WITH_RC4_128_SHA
[C011] TLS_ECDHE_RSA_WITH_RC4_128_SHA
[002F] TLS_RSA_AES_128_SHA
[0035] TLS_RSA_AES_256_SHA
[000A] SSL_RSA_WITH_3DES_EDE_SHA
[0005] SSL_RSA_WITH_RC4_128_SHA
[0004] SSL_RSA_WITH_RC4_128_MD5
and the below are the server side ciphers
server side ciphers available
There was one solution available on google, to replace the localPolicy.jar and US_export_Policy.jar in JDK with the unlimited encryption version. Although I tried the same, but still the same error persist.
Could you please suggest any fix on weblogic10.3.6 server for the same issue or any setting in IE 9.
Early response is highly appreciated.
Regards
Chandra
After posting it I noticed that server side ciphers are not shown in previous post so adding them below
Hi Chandra,
This is not an administration port issue; it’s an SSL issue, you’re getting error because yous key size and JDK JKS is inappropriate. You can import WebLogic 12c JKS to WebLogic 11g; but it’s quiete hard to it. Please email me error logs.
Nice Blog